

Can we fight mass surveillance with antitrust laws?
An ongoing discussion with Cory Doctorow.So We Got Tracked Anyway
Researchers find out, Facebook and Google have been using HTTPS
session IDs incorrectly — in a suitable fashion for tracking
all of those people that have been using Cookie filtering tools
to avoid tracking. Read on.
You're My Victim: Nastiest Scam Ever Encountered
Today, Thomas Miller received the
nastiest scam mail he ever saw.
Regulating technology isn't just a question of saving democracy
from the Internet, it is also about stopping the empowerment of
total strangers to ruin each one of our lives — one by one — individually.
Because what that scam mail is threatening to do, can be done for real.
Policy Recommendations for a Civil and Democratic Digital Future
You may have heard before, that It's 5 years since the Snowden revelations
|
Very few things have improved, most of all humanity has accepted to be living in a post-democratic society in which its basic agency as an electing sovereign is undermined by psychological operations either on a collective level or on an individual level. Half a year ago there was a buzz about this anniversary going to be a big thing and now it just silently passed without much ado. What happened to all the planned events and media coverage? Where is the dedicated documentary that was shot at 34c3? |
A radical proposal to keep your personal data safe
|
The surveillance imposed on us today is worse than in the Soviet Union. We need laws to stop this data being collected in the first place. Read the article by Richard Stallman. |
New videos from ChaosWest 34c3
- Privacy-Oriented Distributed Networking for an Ethical Internet, including 50 Subsystems of GNUnet
- net2o: GUI, realtime mixnet and ethical micropayment with efficient BlockChain
- Scalable and Privacy-Respectful Distributed Systems - Our Chance to Avoid Cloud Computing? (secushare)
- Nextcloud End to End Encryption
- Modeling Trust in a Distributed Private Social Network (secushare)
- P2P with JavaScript to defend against bad lawmaking
- Scuttlebutt introduction
- Three and a Half Ways to Enhance Metadata Protection Beyond Tor (secushare)
THE PROJECT MAP
Here's a map of projects working in some architectural layer of a possible GNU Internet. As you can see, none covers all required layers, so there is some work left to be done:
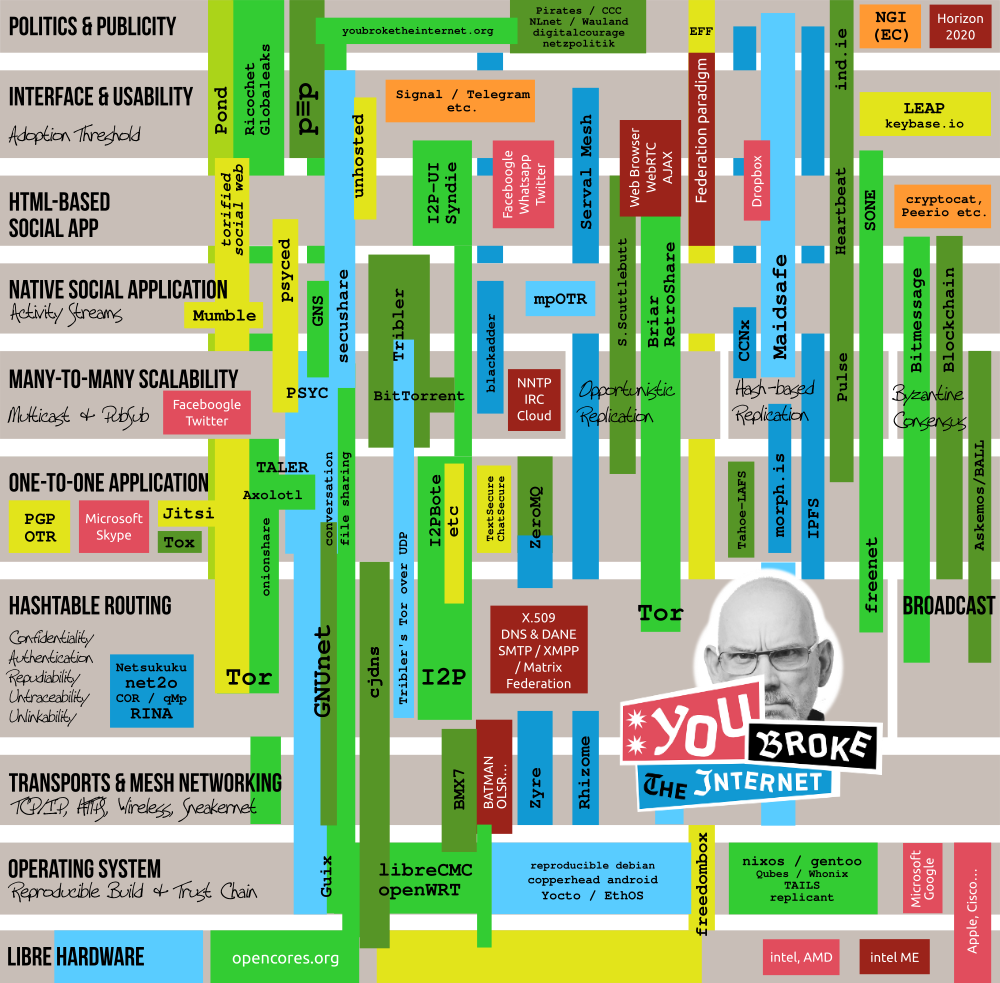
Blue is for projects in development while green is for those that are available. Yellow to red illustrates technologies that probably need to be obsoleted. See the map page for a properly detailed description. Last update in 2018-06.
Architecture for a GNU INTERNET
|
The summer of 2013 will remain the moment we finally realized
how
broken the Internet
was, and how much this had been abused. At first If deployed on top of technologies that were not designed for it, end-to-end encryption has proven to be "damn near unusable," as Edward Snowden put it, let alone forward secure. But there are actually many new tools that have that feature at their foundation. Antiquated protocols like DNS, SMTP, XMPP and X.509 leak so-called metadata, that is the information of who is talking to whom. Also they put user data on servers out of the reach of their owners. X.509, the certification system behind HTTPS and S/MIME, is broken and allows most governments and even many companies to run man in the middle attacks on you. The trust chain between the cryptography and the domain names is corrupt. Even if DNSSEC and DANE try to improve the security of DNS, they still expose your interest for certain resources. SMTP is so hopeless, you shouldn't even use it with PGP and XMPP fundamentally has the same problems: as long as all involved servers know all about who is talking to whom, it is already by far too much exposed knowledge — even if the mere encryption of the connection, which again depends on X.509, hasn't been undermined by a man in the middle, which is hard to find out if there is no human intervention and no reporting to the actual users when servers pass messages between each other. This is not the way it has to be. We believe a completely new stack of Internet protocols is not only feasible, it already exists to a large extent. It merely needs better attention. Currently the majority of technology people are focused on improving the above mentioned protocols, even though they are broken by design… and can only be improved in some partial aspects. Vastly insufficient compared to what humanity deserves. This project is for those who want to look into a future of an Internet, which actually respects constitutional principles and returns democracy to a mostly functional condition. Yet, nothing of this comes about if we don't provide incentives. Without incentives, Internet companies find no business model in protecting fundamental principles of democracy. Whereas universities have already delivered several decades of excellent research and working prototypes in this field, but they aren't incentivized to produce an actually deployable product. Also standards organizations are powerless if the company that infringes civil rights the most is the one that will dominate the market. In practice, competition is at odds with philanthropy. Currently it takes enthusiasts to fill in the gaps between what researchers and companies have released and turn it into something that actually works for the population. We think we need incentives to polish the protocol stack of a GNU Internet, and by GNU we mean that the involved software needs to be free as in free speech, and that we need regulation to actually deploy an upgrade of the Internet to a version that protects its participants from eavesdropping and social correlation. The lawless internet will always be more profitable than the one that respects what's left of democracy, just like it is economically more profitable to send minorities into concentration camps. It takes political will to disallow unethical business models. If only the new Internet is legal, then the opportunity of commercial gain is equal and ethical for all. Nothing is lost. All the industry should embrace this, as only the monopolists need to find themselves new business models.
A video presentation of the |
Proposal for LEGISLATION
|
Bart Preneel suggests (article in German) Europe should invest in an open source infrastructure for secure routing, secure communication and decentralized storage. We started working on a EU law proposal to require mandatory anonymised, authenticated and end-to-end encrypted communications in all telephony and computing devices sold after 201x. Communications shall be anonymous in the sense that third parties are not entitled to recognize who is talking to whom yet they should be authenticated to all of the participants of any conversation, thus cutting out several vectors for so-called „cybercrime” such as unauthenticated SPAM mail, possibly containing malware or viruses. Whereas when interacting with companies, people can choose whether to stay anonymous, assume a pseudonymous identity or authenticate as a legal person. This provides for a much safer way to do business over the Internet, saving citizen and especially companies precious time and money in extra security measures. In particular the failed concept of the password as an authentication scheme can be abolished once cryptographic authenticity is implicit in all transactions. We recommend the pervasive deployment of TALER for anonymous (micro)payments, allowing users to pay for their access to the net anonymously. We hereby determine the Internet to stop being a product and start becoming an existential public infrastructure. We enable the design of "constitutional smartphones" that disallow bulk location tracking by authorities, but we also envision strategies to allow for law enforcement within constitutional boundaries, technologically impeding mass surveillance of entire populations, yet permitting monitoring of individuals following a court order. ioerror has recently formulated similar ideas, albeit with a different strategy. We shall include ways to ensure the correct implementation of such a regulation and a transition path from the existing unsafe systems. Be aware that this initiative, as a side effect of reconstructing the constitutionality of the Internet, resolves aspects of net neutrality, data protection and data retention all as an inevitable and logical side effect. DG CONNECT of the European Commission has expressed informal interest in this proposal, but suggests that it should find more public backing in order to find its way into the regulatory process. So now it is your turn, dear reader, to help promoting this. You can examine the current draft in ODT (free) or PDF (proprietary) format. Previous versions are listed here. In 2017 there has been an introductory presentation of our legislative ideas at the pirated security conference in Munich. |
Publications
Siehe auch: |
What do you do if the "extremist views" you once represented in the wake of the Snowden leaks are now a position discussed in the European Commission?
| “ |
The Next Generation Internet is not just a functional enhancement or mere optimisation of the current internet. The NGI is a necessary high level effort to overcome the fundamental trust crisis the internet has been pushed into in 2013 after whistle-blower revelations detailing major abuse and large scale exploitation of internet trafic. From a policy and technology point of view the integrity of the entire system is currently breached. At the IAB plenary of the 88th IETF Bruce Schneier remarked: “The Internet has largely been run as the United States benign dictatorship, because everyone kind of believed the United States was acting in the world's best interests. That's over“. We now have to deal with the unwelcome aftermath of the double intent with which the internet was brought into the world. The US government promoted the internet across the globe as a major contribution to humanity, claiming it would help spread freedom and knowledge everywhere. Yet elsewhere in government it consciously decided to abuse that trust, and succeeded in doing so at an unprecedented scale. In retrospect, the internet has served as an immense trojan horse – one of the greatest espionage successes recorded in history. This hidden agenda successfully delivered decades of mass surveillance capabilities at global scale. The current weak core architecture of the internet and many of its legacy infrastructure components are to be considered fundamentally untrustworthy as a result. Action is needed to amend that situation. The internet of today exhibits intrusive behaviour by nation states as well as commercial and extralegal actors. The negative effects of the geopolitical double play have been reinforced by a skewed and predatory market driven by greed and lacking ethical considerations shared across Europe. The factual result is an almost complete surrender of autonomy: in the context of the internet, the web, the mainstream operating system market for desktop and mobile, content discovery and delivery, e-payments and the cloud. There is a small set of dominant actors which have successfully hijacked the course of the internet as once envisioned – although it could be argued that this was a fictional situation to begin with. There is no alignment between what is good for society and the internet that is overgrowing the globe. Succinctly put: we need trust built from the ground up. Every technical primitive from the current internet needs to be re-evaluated in terms of the complete threat catalog, as we cannot afford our multi-trillion euro economies and societies to not be able to trust the internet as we move forward. We need a Next Generation Internet that – beyond any doubt – is dedicated to the public good, which is (re-)engineered and professionally audited to achieve solid trustworthiness and transparency in all aspects of its operation. | ” |
|---|
"NGI. Suggested topics for EC DG-CONNECT." Page 7.
Discussing the Next Generation Internet at the 34c3
|
|
Expertise for a Next Generation Internet
|
|
Pointless? Hopeless? Or a chance to save democracy?
|
We're not the first to say the Internet has turned into the greatest threat to democracy. The measures society has to take, to ensure civil rights and freedom aren't at stake, are likely drastic. More than most would want to believe. It probably takes both better technologies and better laws. On May 6th, 2016, at Berlin's Onionspace, the office space for projects that intend to fix the Internet, we hosted a political discussion regarding the use of scalable, distributed and GNU technologies as a possible way to recover some bits and pieces of democracy. Is this all pointless? We invited alert minds to ask us and the audience some tough questions. Participants in the discussion were:
Audio recording of the discussion:
|
YBTI after the 33c3 Hacker Congress
|
We did our best to Fix the Net at the 33c3, but since that is never enough, We Meet Again on January 2nd in Berlin, from 14:00 to 20:00 hours, at our favorite Onionspace. |
YBTI at the 32c3 Hacker Congress
|
Once again, here we were – and these were the times. Bernd has recorded some videos for us to watch. |
Before, during and after the Camp 2015
|
The Chaos Communication Camp has become an almost inevitable place of exchange and shared evolution every four years. We held a long list of sessions at the "We'll Make us a Gnu One" project located by La Quadrature du Camp. We also had meetings and hack-on sessions after the camp in Berlin. One of the outcomes is the port of GNUnet on OpenWRT for the purpose of having a libre cryptographic routing system on mesh networks. |
Workshop at Opentechsummit 2015
|
Always driven by convenience and easy solutions, the Internet and digital networks such as telephony's GSM have evolved into the easiest platform for a complete surveillance of humankind. This has some practical aspects when your priority is to hunt down crime, but by giving the power of omniscience to certain government agencies the Montesqueuian principle of Separation of Powers has been undermined. Foundational values for a successful exercise of Democracy, such as the Secrecy of Correspondence or the Freedom of Assembly, which is effectively deanonymized and thus abolished by metadata collection, are impeded. In a situation of continued observation, the Freedom of Expression suffers by consequence. Even parts of the European Commission agree, that unregulated technology has positioned us on a slippery slope leading us into a neo-totalitarian society. Surprisingly though, this doesn't have to be this way. By combining advanced technology and insightful legislation, it is up to the parliaments in power to priorize correctly and choose whether democratic preconditions are to be valued over law enforcement convenience. We discussed options for a combined legal and technological framework that defines a GNU Internet, designed to protect constitutional principles of democracy, yet allows for targeted law enforcement within democratic boundaries. As a side effect it should also provide a more secure way for people to do business over the Internet and cut out several vectors for "cybercrime." |
Videos from the YBTI Sessions at 30c3
Next generation appsThe next generation on privacy and crypto apps all satellite around public-key based routing. We'll discuss e-mail replacements, secure telephony and DHT-based storage systems.
UsabilityHow can we make our technologies grandpartent compatible and the exchange of cryptographic keys and shared secrets a natural everyday transation?
Futures of Public-Key based RoutingHow can something like onion routing become a basic function of the Internet? How can end-to-end authenticity be the default?
Scalability of Distributed SystemsWhy is it so hard to do a distributed Twitter that actually works?
Mesh NetworkingWe need more infrastructure that is run independently of nation states or for-profit corporations. Who owns all the wi-fi gear in our homes? Is it them or us? How can we as a society operate networks for the common good?
Secure Name SystemsThe great shoot out panel of the name resolution titans. Does it make sense to patch the Domain Name System? Which strategy should we pick for a safer new Internet stack? Should we require cryptographic privacy of name resolution?
Additional in-depth presentations
Operating SystemsFrom safer use of cryptography over kernel magic to reproducible compilation of to a vision of a full security redesign of the OS.
Libre HardwareIf the hardware we are running our systems on is intrinsically insecure, we may be building a fortress on top of a house of cards. What is required on the lowest levels to obtain reasonable endpoint security? Very interesting panel featuring illustre guests:
Summary of the 30c3 YBTI SessionsSummary + discussion on the legislation proposal for obligatory obfuscated and end-to-end encrypted communication: (webm, mp4) |
Best Practices for Crypto
|
We have published our revised version of the comparison report on Options for a Secure Mail System originally written by Elijah Sparrow of the LEAP project. It discusses plenty of legacy protocols and legacy-oriented proposals such as LEAP itself and why very unfortunately they are unlikely to solve the issues at stake. Then again you may find Best Practice Recommendations for Crypto Tools much more interesting as it spans all use cases and is more to the point. |
Video: Knocking down the HACIENDA
|
This is "Knocking down the HACIENDA," the talk from the GNU Hackers Meeting 2014 that caused some mayhem for making the GCHQ HACIENDA program generally known to the public. The talk details how the five eyes agencies have been collaborating to systematically obtain control over computers on the entire planet, and how the new TCP Stealth technology developed by the presenter provides obstacles to the massive port scanning. GNU Internet technologies should support this new advanced TCP port knocking technique. |
Workshop for a GNU CONSENSUS
|
On the week-end of August 24-25, 2013, we gathered at Berlin's CCC headquarters to develop a rough consensus on what the criteria should be for a GNU internet and to prepare for the upcoming sessions at 30C3. |
Video: Talks for a GNU INTERNET
|
This is the video from the talks given in Berlin on August 1st, 2013. Over 100.000 people have watched it already — so should you. The talks are in English, even though the welcoming words are in German. ... featuring:
Christian Grothoff's talk summarized the recent revelations about PRISM and their implications for non-American citizens, industries and governments. It then presented technical solutions towards a secure and fully decentralized future Internet, which would address key challenges for self-determined life created by the world-wide police state. Interesting details on this:
Carlo von lynX gave a presentation on how secushare intends to provide messaging and Facebook-like functionality on top of GNUnet. Keywords:
Richard Stallman and Jacob Appelbaum reminded the audience of the relevance of free software, free hardware and the pervasive use of cryptography and responded to questions. Denis and Torsten spoke introductory and closing words. This event was kindly hosted by the Piratenpartei Berlin. |
ASKED QUESTIONS
|
WE'RE NOT ALONE
|
Back in 2013, just after the Snowden leaks, we seemed to be the only crazy people to ask for these things.. a systematic overhaul of the Internet.. an immediate upgrade from merely encrypted communications to metadata-protective communications. Our idea that servers aren't a safe place for such data was considered radical, even just after the new findings, but to us it was clear there was not another day to lose. In the meantime more political projects promoting these technologies have sprung up with very similar objectives, not counting the software projects themselves, which started heading in the right direction already a decade before. So let us recommend you also inspect EDN, the mesh networking oriented sister of YBTI and the Counterantidisintermediationism project (also known as e2einit). 2017, the Pirates and ind.ie are involved. The NLnet Expert Group is consulting the European Commission in regards of a Next Generation Internet project, that sounds as if they responded to our call for incentives. |
GET IN TOUCH
|
If you're already using Tor software you can meet us in our chatroom via our onion service:
Otherwise, here are more traditional means:
We hope our chat service to be reasonably safe, but there's still a risk that your interest in us is exposed, or even the contents of the chat ends up in the wrong hands. We may occasionally make public announcements in the unsafe Internet:
|